Recently I encountered a Web Application Proxy (WAP) server that was stuck in a failed state after changes to the ADFS backend service.
In the Remote Access crimson log on the WAP server, an event 422 error appeared once every minute, showing that the WAP server could not retrieve proxy configuration from the ADFS backend server:
Log Name: AD FS/Admin
Source: AD FS
Date: 12/26/2016 8:40:46 AM
Event ID: 422
Task Category: None
Level: Error
Keywords: AD FS
User: NETWORK SERVICE
Computer: WAP.adatum.dk
Description:
Unable to retrieve proxy configuration data from the Federation Service.
Additional Data
Trust Certificate Thumbprint:
B421507C4504922646A1840CB81E915E6F1CE6B6
Status Code:
Unauthorized
The WAP configuration is stored and should contain information about all published web applications, so in many cases a reset and reconfiguration can be the fasted approach for restoring the WAP server into working state.
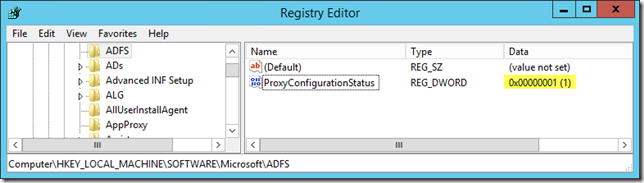
To do this, open the Registry editor (regedit.exe) and browse to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ADFS
Here modify the ProxyConfigurationStatus REG_DWORD and change the data value from 2 to 1
From here you can either restore the WAP configuration using PowerShell, as demonstrated in this post Resolving Web Application Proxy error code 0x80075213, or you can run through the Web Application Proxy Wizard, which I will show in this demonstation.
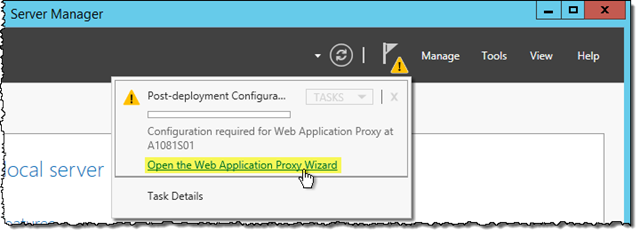
On the WAP server, open Server Manager and click the Refresh dashboard icon (the round “yin-yang”-like icon)
Click on the Open the Web Application Proxy Wizard link
Click Next
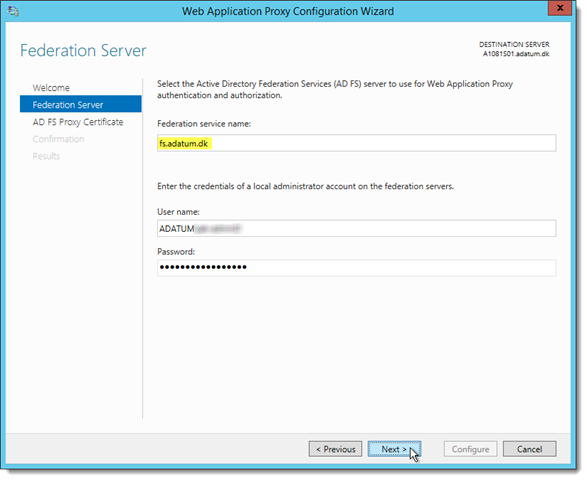
At the Federation Server page, supply the requested information:
- In Federation service name:
Enter the address of the Federation service name, like fs.adatum.dk - In User name/Password:
Enter the internal/corporate domain credentials for an account that is member of the local Administrators group on the internal ADFS servers – this does not have to be the ADFS service account.
or
Enter the internal/corporate domain ADFS service account credentials, as used during the ADFS configuration.
NOTE:
These credentials will only be used once in order to create a proxy trust, and they are not stored.
Click Next
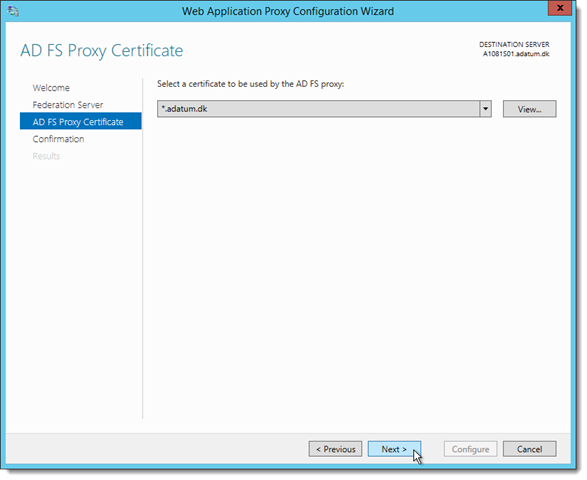
On the AD FS Proxy Certificate page, select a certificate to be used for AD FS proxy functionality.
The certificate selected here should be the one that whose subject match the Federation Service name, for example, fs.adatum.dk or *.adatum.dk.
The wizard will display a warning if an expired or invalid certificate is selected.
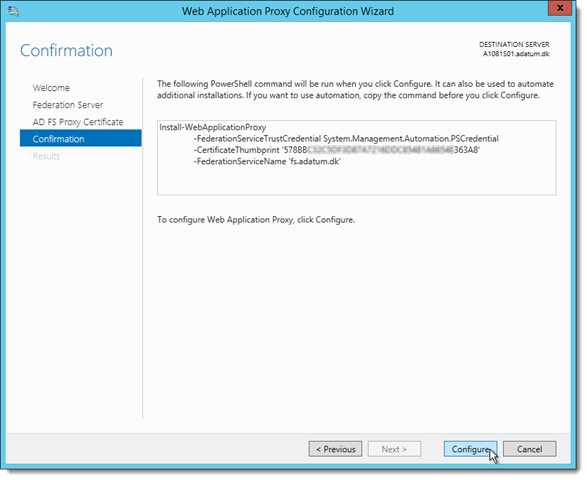
Click Next
Click Configure
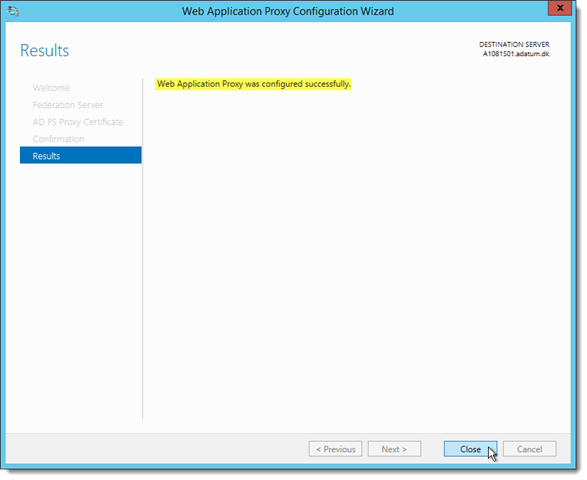
Wait until the Web Application Proxy Configuration Wizard has retrieved the ADFS configuration and completed the WAP configuration – this may take from a few seconds to a few minutes …
Click Close
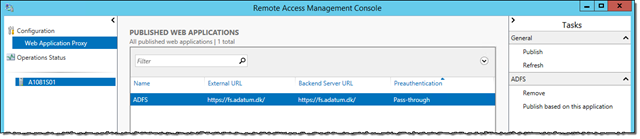
After closing the Web Application Proxy Configuration Wizard, the Remote Access Management Console automatically opens, and should also load previously published web applications.
If the WAP configuration does not contain any published web applications, follow the last step in this post How to install and configure Web Application Proxy for ADFS to publish the ADFS and other relevant services.
Logon to any other WAP servers in the same cluster, and repeat the above described process to re-configure Web Application Proxy.