As part of the Microsoft Secure Future Initiative Microsoft have started enforcing the use of Multi-Factor Authentication (MFA) for all users when accessing certain portals and services.
First in line to be included are Azure portals and services, with Microsoft 365 following in 2025.
Enforcement phases
Beginning October 2024, Microsoft started phase 1, where MFA will gradually be required in all tenants worldwide for sign-ins to:
Early 2025, Microsoft will move on to phase 2, where MFA enforcement will gradual be rolled out for sign-ins to:
From 03. February 2025, Microsoft will start enforcing MFA for sign-ins to the Microsoft 365 admin center portal
Important:
- MFA enforcement also include emergency access/break-glass accounts.
- Microsoft Graph PowerShell and Microsoft Graph API are not included in the announced MFA requirements.
Postpone enforcement
Although organizations cannot opt out of the MFA requirement, Microsoft allow postponing the MFA enforcement for organizations with complex environments or technical barriers.
Using a Global Administrator account, these organization can open their Azure portal (https://aka.ms/managemfaforazure) and select Postpone enforcement:

Enabling MFA
When enabling users to utilize MFA, organizations can choose among a range of methods, including:
- Microsoft Authenticator
- either push notifications, biometrics, or one-time passcodes.
- either push notifications, biometrics, or one-time passcodes.
- FIDO2 security keys
- external USB, near-field communication (NFC), or other external security key.
- external USB, near-field communication (NFC), or other external security key.
- Certificate-based authentication
- personal identity verification (PIV) and common access card (CAC).
- personal identity verification (PIV) and common access card (CAC).
- Passkeys
- phishing-resistant authentication using Microsoft Authenticator.
- phishing-resistant authentication using Microsoft Authenticator.
- SMS or voice approval
- least secure MFA method.
- least secure MFA method.
- External multifactor authentication solutions
- supported when the federated IdP is configured to send MFA claims.
To enable MFA on an account, the user can simply open the Security info page of the account (aka.ms/mfasetup) and click Add sign-in method
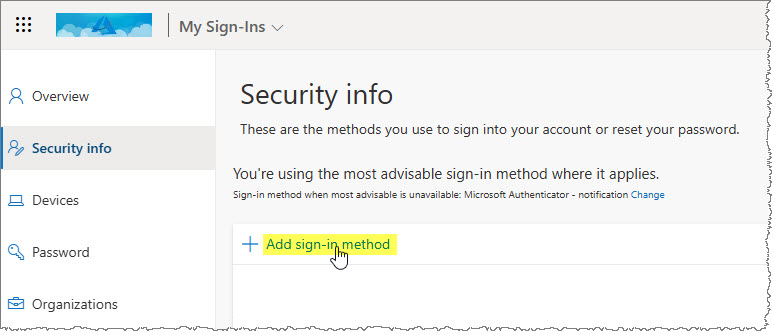
The user now select a verification method, such as the Authenticator app (Microsoft Authenticator).
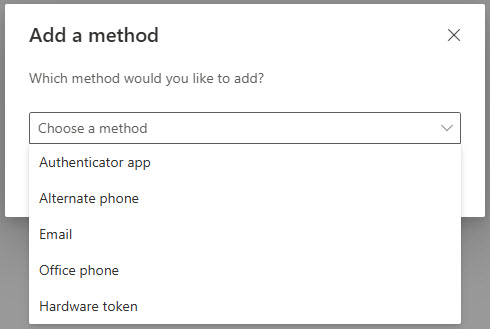
Finally click Add and follow the instructions in the registration wizard.
Organizations can help users get their MFA verification configured by adding all users or selected individuals to a Multifactor authentication registration policy in their Microsoft Entra admin center.

When Microsoft roll out the MFA enforcement to the organizations tenant, users will be prompted to verify sign-ins using their preferred MFA method.
Organizations that have completed one of the following changes in their tenant, will already meet the MFA requirement:
- Enabled Security defaults
- default enabled for tenants created 22. October 2019 or later
- default enabled for tenants created 22. October 2019 or later
- Configured per-user MFA settings
- Enabled Conditional Access policies in Microsoft Entra containing MFA requirements for the relevant portals.