Microsoft recently introduced new features that will enable organizations to get a more integrated collaboration and trust experience between multiple Azure AD tenants.
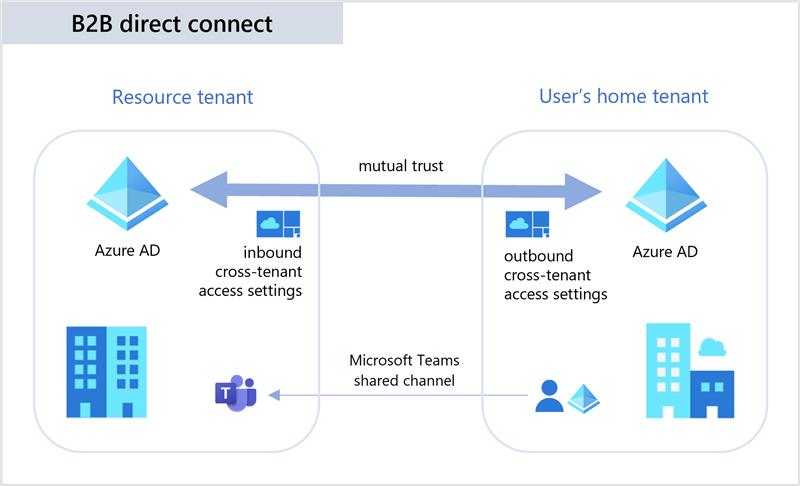
Azure AD now include the B2B direct connect feature that allow you to configure a mutual trust relationship with another Azure AD organization for more seamless and integrated collaboration.
Currently, this feature works with Microsoft Teams shared channels.
With B2B direct connect enabled and configured, users from both organizations can work together in a shared channel in Teams using their home tenant credentials, and without first having to be added to each other’s organizations as guests.
For many organizations the use of multiple tenants is the best option for service or administrative separation, and here B2B direct connect can be used for sharing resources across multiple Azure AD tenants within a single own organization, or to share resources with external Azure AD organizations.
Please note that B2B direct connect requires that mutual trust relationships are setup between two Azure AD organizations to allow users from both organizations to access to resources in both tenant.
Both the resource organization and the external organization need to mutually enable B2B direct connect in their cross-tenant access settings. When the mutual trust is established, the B2B direct connect user has single sign-on access to resources in the external tenant using credentials from their home Azure AD organization.
For mutual trusts, both organizations should be aware to configure both inbound and outbound access settings, to allow internal and external users to access resources in both tenants.
Pricing
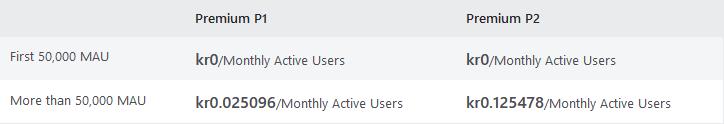
Azure AD External Identities pricing is based on Monthly Active Users (MAU):
- Your first 50,000 MAUs per month are free for both Premium P1 and Premium P2 features.
- A flat fee of DKK 0.232 is billed for each SMS/Phone-based multi-factor authentication attempt.
Configuring B2B direct connect
Sign in to the Azure portal using an account with either the Global Administrator or the Security Administrator role
Select External Identities and then select Cross-tenant access settings
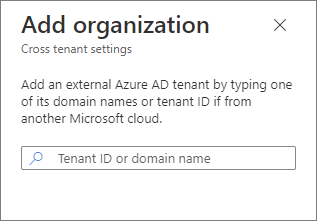
In the Organizational setting blade, click Add organization
Enter either the Tenant ID or the full tenant domain name (.onmicrosoft.com), review the organization and then click Add
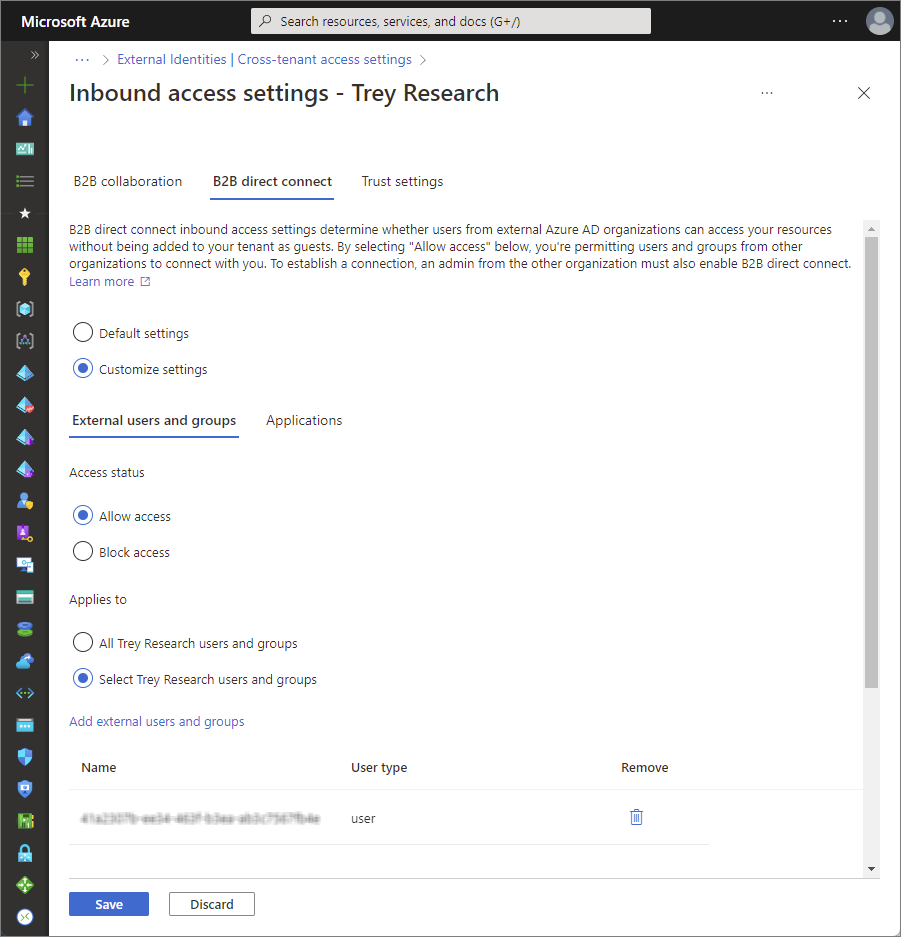
At first when an organization is added the access settings are inherited from the Default settings.
To change the settings for this particular organization click on the Inherited from default link under either Inbound access or Outbound access.
Inbound settings:
Which external users and groups will be able to access the selected internal applications.
Outbound settings:
Which internal users and groups will be able to access the selected external applications.
Select the B2B direct connect blade and modify the appropriate settings for External users and groups, and for Applications.
When complete click Save
The default settings for outbound B2B direct connect is set to All blocked, so for configuring mutual access between two tenants, ensure that both Inbound access and Outbound access is changed to allow internal users to access resources in the external tenant.
Please note that for privacy concerns, configuring B2B direct connect will enable users in the external organization to search for home tenant users by full email address, and the matching search results will return the first name and last name of these users.
Ref.: